Malware
Malicious software or malware is a program or file that is harmful to a computer user. Types of malware can include computer viruses, worms, Trojan horses and spyware. These malicious programs can perform a variety of different functions such as stealing, encrypting or deleting sensitive data and monitoring user’s computer activity without their permission.
Attackers will use a variety of methods to get malware into your computer, but at some stage, it often requires the user to take an action to install the malware. This can include clicking a link to download a file, or opening an attachment that may look harmless (like a Word document or PDF attachment), but actually has a malware installer hidden within.
Phishing
An attacker may send an email that appears to be from someone you trust, and the email will seem legitimate, and it will have some urgency to it. In the email, there will be an attachment to open or a link to click. Upon opening the malicious attachment, you’ll thereby install malware in your computer. If you click the link, it may send you to a legitimate-looking website that asks for you to log in to access an important file, but the truth is the website is actually a trap used to capture your credentials when you try to log in.
Denial-of-Service (DoS)
A denial-of-service attack is a security event that occurs when an attacker prevents legitimate users from accessing specific computer systems, devices, services or other IT resources. DoS attacks typically flood servers, systems or networks with traffic in order to overwhelm the victim’s resources and make it difficult or impossible for legitimate users to access them.
SQL Injection Attack
Many of the servers that store critical data for websites and services use SQL to manage the data in their databases. A SQL injection attack specifically targets this kind of server, using malicious code to get the server to divulge information it normally wouldn’t. This is especially problematic if the server stores private customer information from the website. An SQL injection attack works by exploiting any one of the known SQL vulnerabilities that allow the SQL server to run malicious code.
Cross-Site Scripting (XSS)
This attack involves injecting malicious code into a website, but in this case, the website itself is not being attacked. Instead, the malicious code the attacker has injected only runs in the user’s browser when they visit the attacked website, and it goes after the visitor directly, not the website.


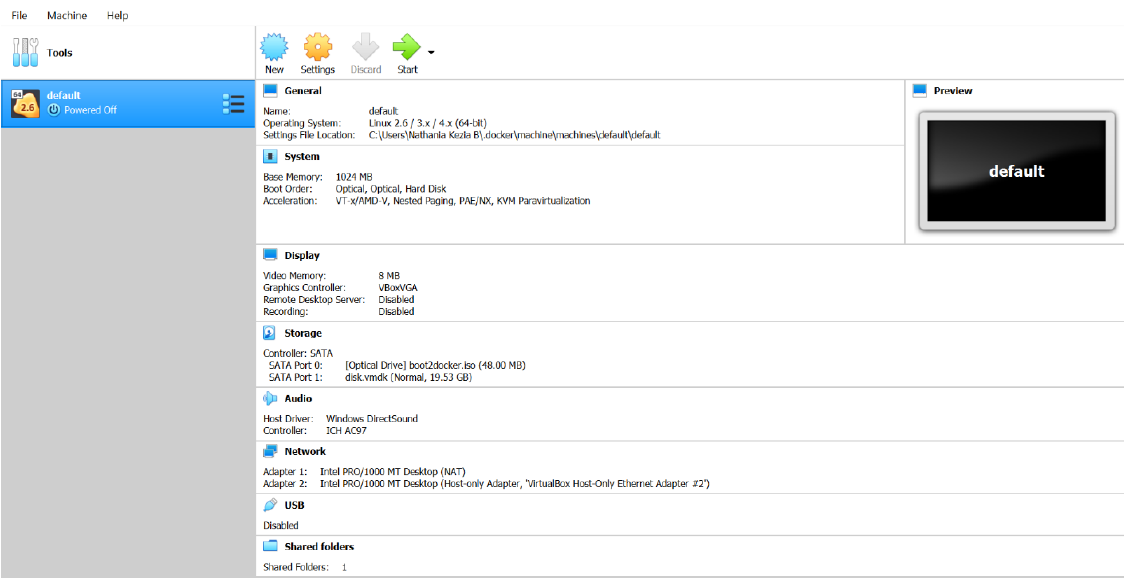
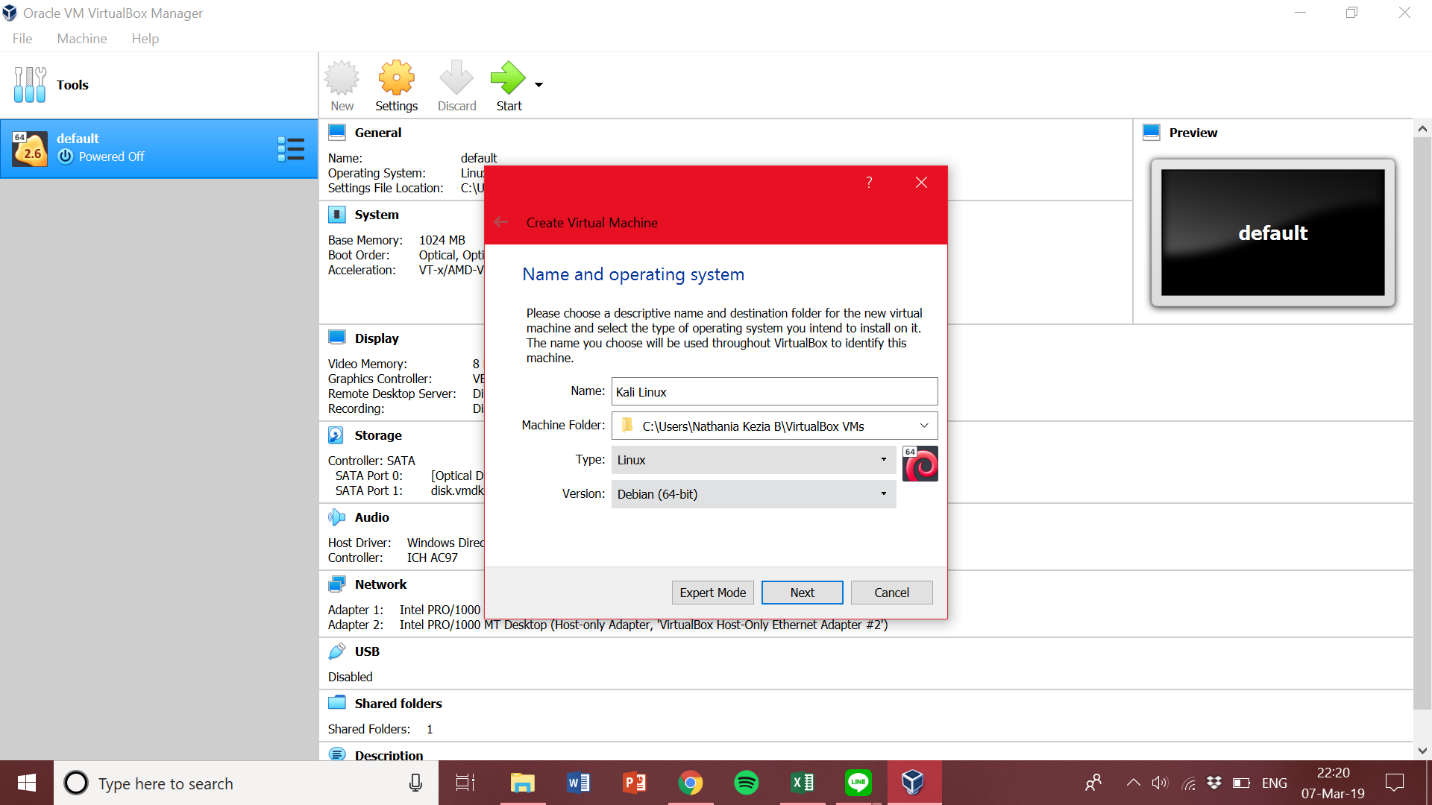
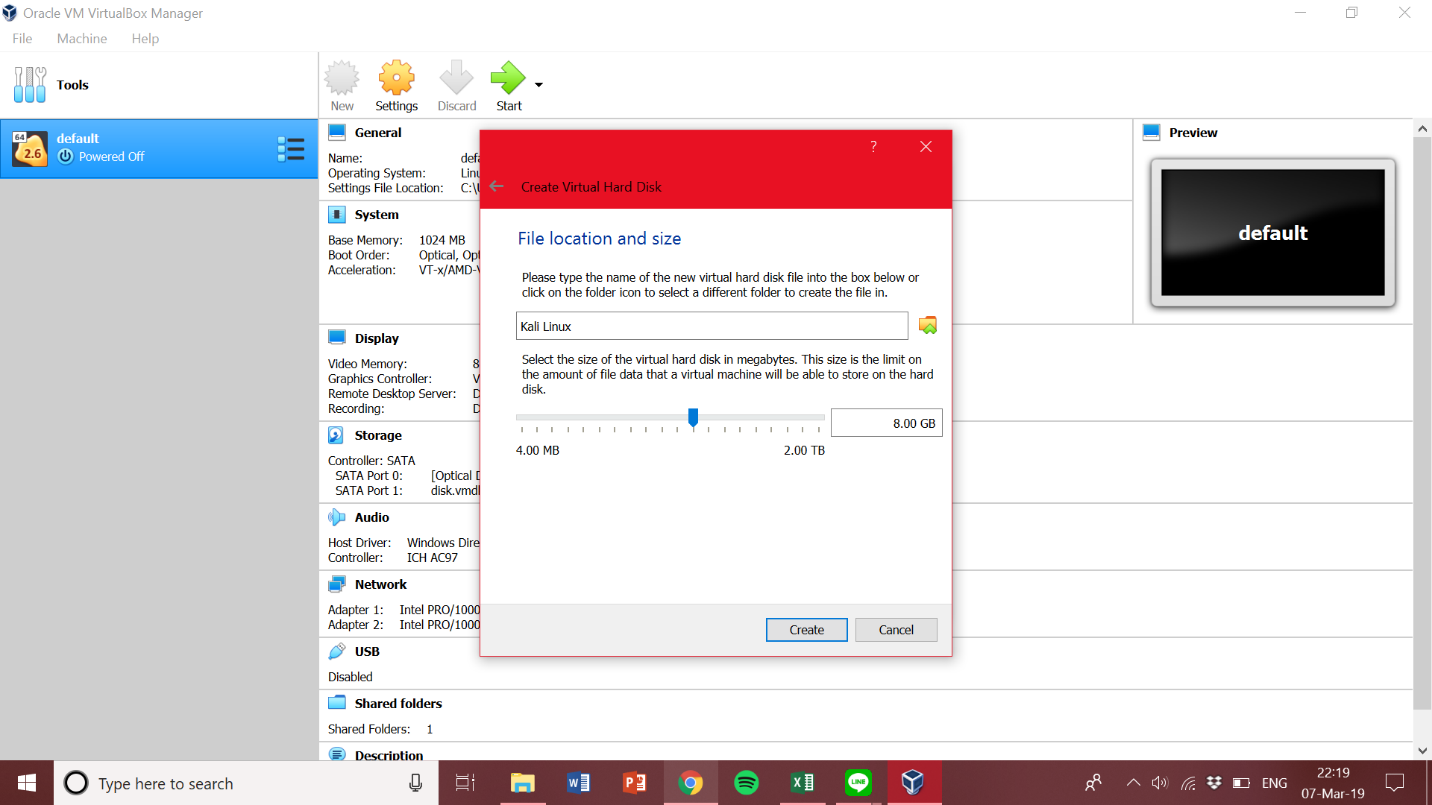
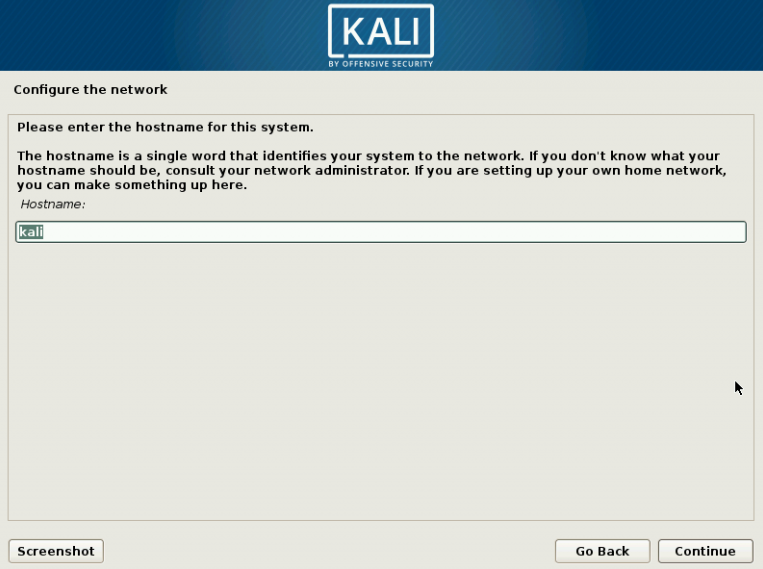
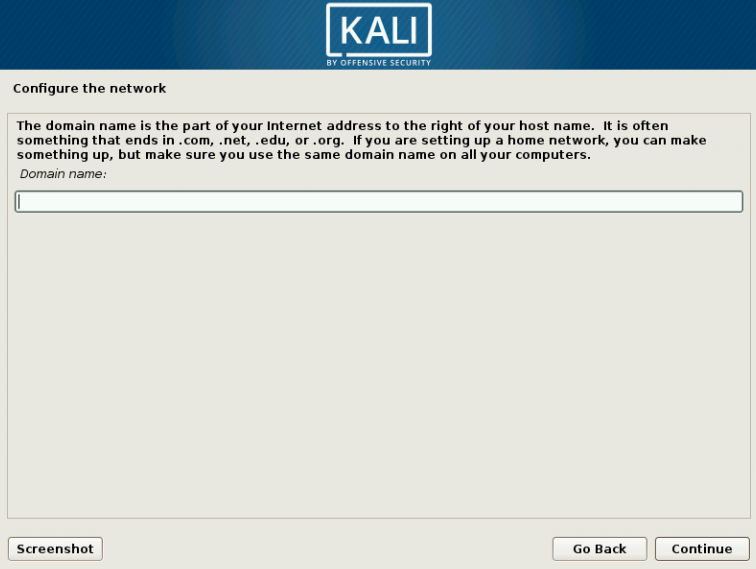
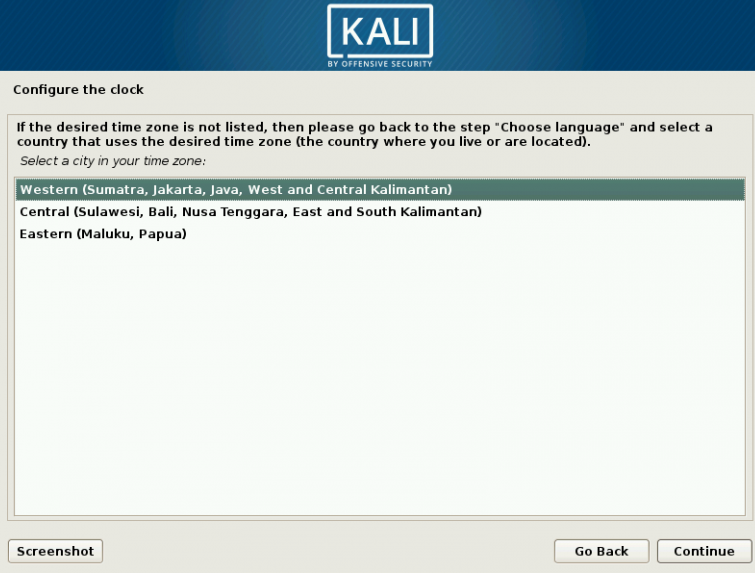
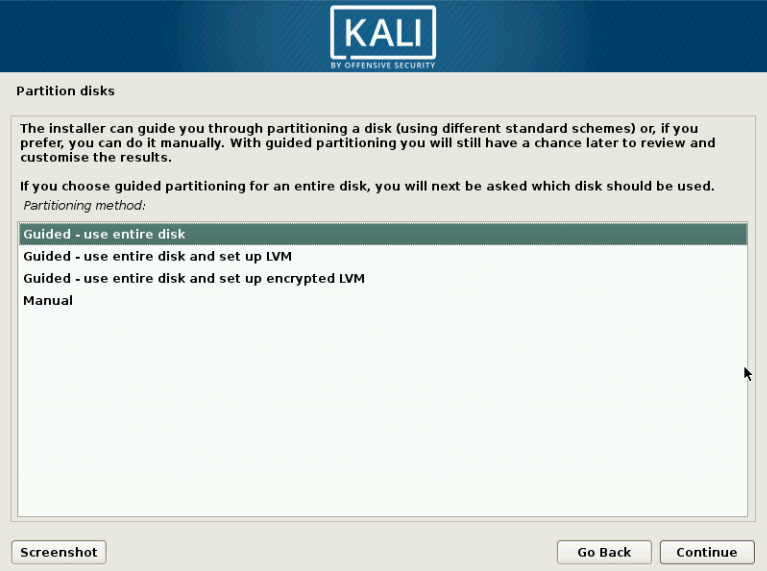
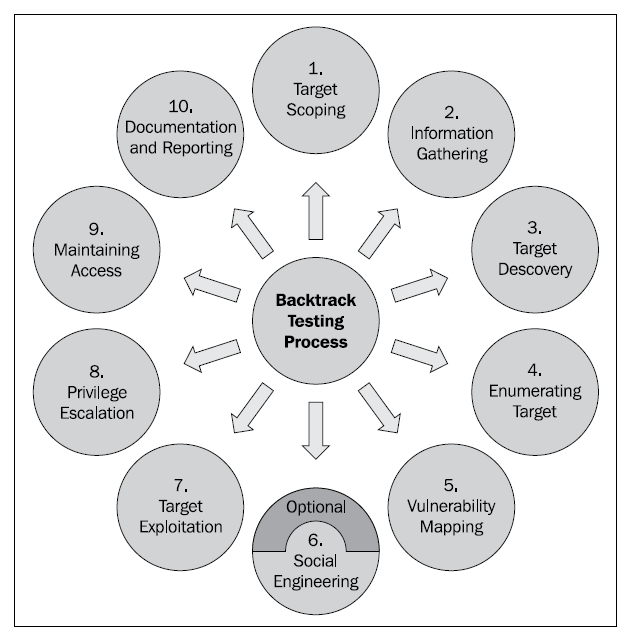 1 Target scoping
1 Target scoping