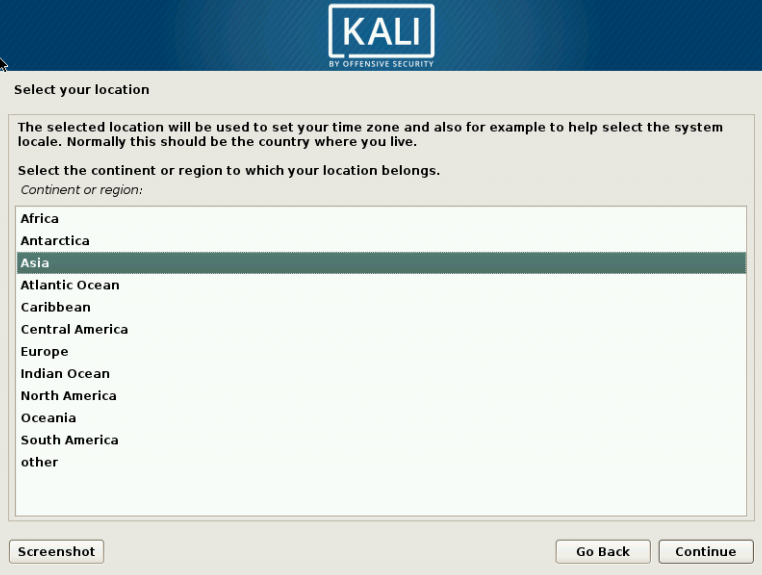
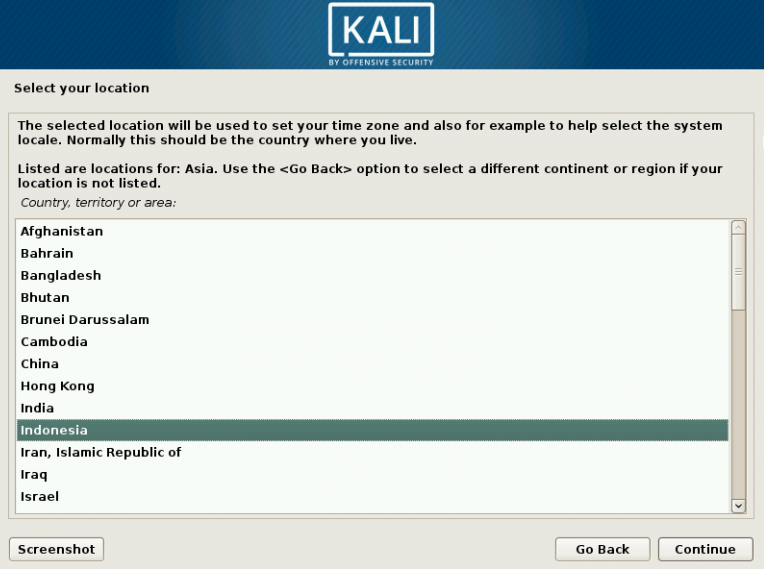
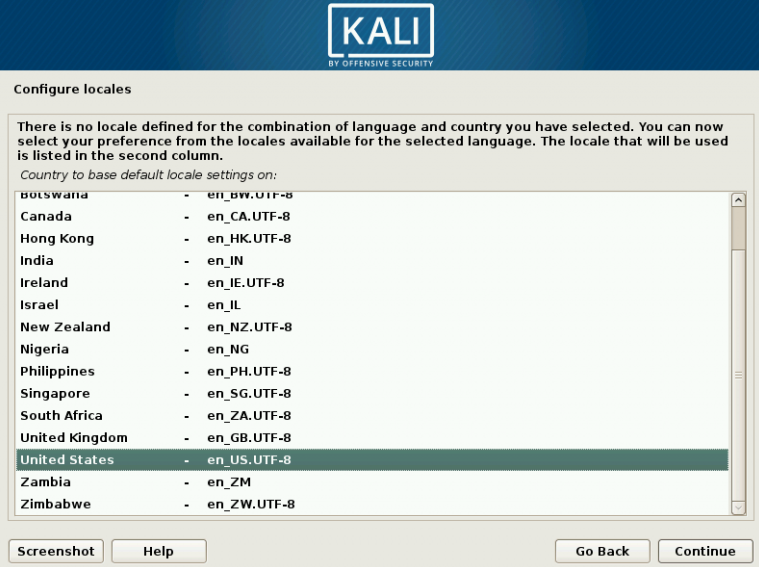
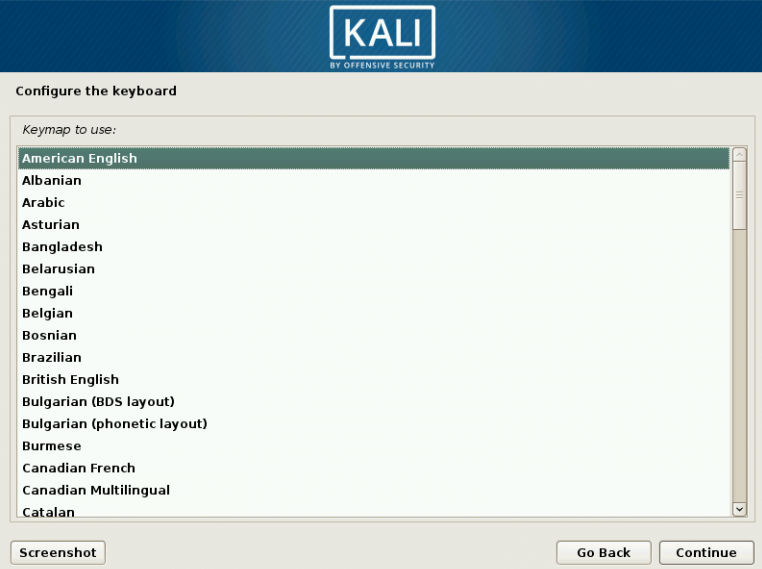
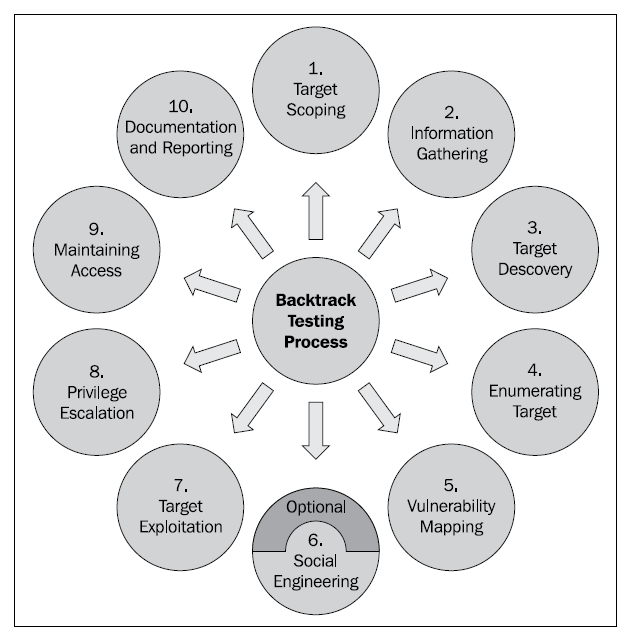
 1 Target scoping
1 Target scoping
In this step, we observe the network condition and determine what to do. What objectives we need to achieve, how long does the test going to take, etc.
2 Information Gathering
Gather and learn about the target from public sources, such as Google, Yahoo!, and many more. Information gathering can also be done with footprinting tools.
3 Target discovery
in this step, we mostly deal with identifying the target’s network status, OS, and network architecture.
4 Enumerating target
Find open ports of the target. Once the open ports have been identified, they can be enumerated
for the running services.
5 Vulnerability mapping
Identify the weakness of the target based on the disclosed ports and services.
6 Social Engineering
Manipulate target into executing malicious code that gives access to the auditor. This step is optional.
7 Target exploitation
In this step, we really penetrate into the system. This step focused on the target acquisition process that has three core area, includes pre-exploitation, exploitation, and post-exploitation activities.
8 Privilege Escalation
The goal of this step is gaining the highest level access of the target.
9 Maintaining Access
Keeping control of the target for a specified amount of time. Provides a clear view of how an attacker maintains access without noisy behavior.
10 Documentation and Reporting
Documenting, reporting, and presenting the vulnerabilities found.